DURHAM, N.C. — When the hackers started calling Duke University students on the phone, Nick Tripp knew he was dealing with something different.
Tripp is the senior manager for the Duke IT Security Office. He’s used to dealing with the daily phishing emails and other attempts to get into the university’s computer system. It’s an attractive target, a major research university and a big hospital.
Duke uses what’s called “double-factor authentication” for students, staff and faculty to log in to the university systems. After entering their password, users must also use a randomly generated security code from an app or text message.
It’s an important layer in the university’s security. Most big organizations now use some sort of double-factor authentication.
That’s how Tripp found himself on the phone with a man with an eastern European accent at about 11 p.m. on a Thursday in September.

“That was definitely a surreal moment for me,” Tripp said. His team had been dealing with this active attack in their system for 14 hours already. “Everybody would prefer to be in bed, and I'm on the phone with the person who's keeping us all up.”
The attack worked like this: the hackers sent out thousands of emails crafted to look like it came from Duke’s IT desk, warning that the user’s email account would be deactivated unless they clicked on a link. It instructed people to put in their name, login, password and phone number. Then the hackers would call the user to get the double-factor authentication codes in real time to be able to log into Duke’s system.
“They were hoping to capture multi-factor authentication credentials, which is really difficult to do via form,” Tripp said.
“They were calling our users and pretending to be our service desk,” he said. “I had to pose as a user and call them and say, ‘Hey, I've filled out the form. What's next in this process to figure out?’”
“They were really, really helpful right up until the moment that they thought they got that information from me. Of course, I gave them fake information, but as soon as they thought they had it, they were done and off the phone, immediately hung up and onto the next next call,” Tripp said.
Anyone who has an email account knows there are constant messages trying to bait people into clicking on suspicious links. That’s known as “phishing,” when bad actors send emails in an attempt to get someone to download an attachment or click on a link, often installing malware that gives a hacker access to their target’s computer.
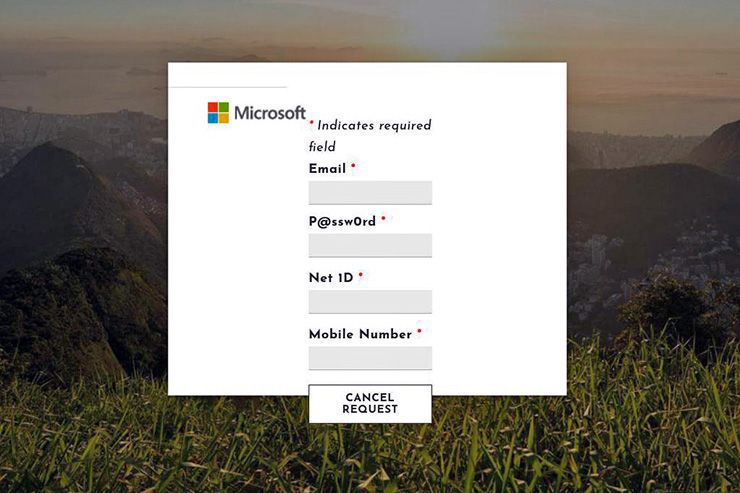
The attack Tripp described at Duke was a phishing attempt, with the added layer of calling users at Duke for those multi-factor authentication codes. The hackers made some progress getting into email accounts, but the university’s security team was able to identify those accounts and shut down access, according to Duke.
“We are constantly under attack,” Tripp said. “That's something we have to be ever-vigilant about, because it never stops. I mean, the attackers don't take days off and that's a global effort.”
Cybercrime is a global phenomenon. There are organized criminal groups in Russia and eastern Europe, state actors like China and North Korea, and lone wolves around the world.
The threats are just as varied. Hackers may aim to hold data hostage with so-called ransomware attacks. They may be looking to steal personal data to sell on the dark web. They could be trying to get access to proprietary technology and steal trade secrets.
For an organization like Duke University, with a hospital, major research labs and a big network, the target could be anything.
“It's almost impossible to fight back and get ahead of this sort of thing,” Tripp said. “You're out-resourced from the start and, you know, most organizations are just trying to do business day-to-day.”
In North Carolina, there were 1,665 computer security breaches reported to the state Department of Justice in 2022. That’s down slightly from the 1,759 reported the year before, according to the NCDOJ’s annual report on cybercrime.
The number of successful phishing attempts in North Carolina is actually down, at least in the incidents reported to NCDOJ. The department reported a high of more than 300 successful phishing attempts in 2019. That number dropped to 252 last year, according to the report.
“The 2022 cyber threat landscape was defined by persistence, increased target scope and relentless determination,” cybersecurity firm CrowdStrike wrote in its 2023 Global Threat Assessment report. The top three industries at risk of cyberattack are technology, finance and health care, according to the report.
Network defenses are always changing and evolving, but hacker groups are moving even faster to get around those defenses. Firewalls improve, companies fix exploits in their software, new security measures like two-factor authentication all try to keep hackers at bay. But computer security specialists are just trying to keep up.
“It does require you to always be learning and keeping up with the latest,” Tripp said. “For our team that means everyone staying on top of the latest trends, the news and continuing education.”
“It's actually one of the pros of this job, and one of the cons at the same time. I think a lot of IT jobs can be a little bit dull or get repetitive over time and that's never the case in security,” he said.
Good cybersecurity people are in high demand in government and the private sector. Information security analyst, basically a cybersecurity expert, is one of the fastest growing jobs in the United States, according to the Bureau of Labor Statistics.
“With approximately 700,000 cybersecurity positions open, America faces a national security challenge that must be tackled aggressively,” the Biden administration said last year as it convened a White House summit focused on the cybersecurity workforce and training.
In North Carolina, community colleges and public universities are stepping up to train the next generation of cyber defenders. The cybersecurity program has become one of the more popular tracks at Wake Technical Community College.
The school offers two-year degrees, and students can transfer directly into a four-year program at somewhere like North Carolina A&T University or East Carolina University, which has a deal with the college to transfer credits.
Wake Tech also has certificate programs for people already in the industry to update their skills.
The college began offering a dedicated cybersecurity degree about six years ago, said Carolyn DeSimone, director of the cybersecurity program at Wake Tech. The program is based at the college’s Research Triangle Park campus, surrounded by some of the most advanced tech companies in the world.

“Students have two ethical hacking and pentesting (penetration testing) classes, two digital forensics courses. So they know how to extract data from computers, phones, examine it, etc. and then they have security operations center courses,” she said.
“They learn how to function either in a large or small employer in a security operations center. People are being attacked all the time. But is it a real attack? Or is it just you know, somebody who misinterpreted the data? So (they are) being trained to use the tools and examine the data so that they know if it's really, in fact, an attack,” DeSimone said.
An important part of programs like Wake Tech’s, DeSimone said, is how they can retool classes quickly to keep up with trends.
“Well, the good news with the community college, as large as we are, we are extremely nimble,” she said. They have an advisory board made up of people in the industry guiding how courses should be updated to keep up with the latest in cybersecurity.
The college also brings in people from the private sector to teach in the cybersecurity program.
“These are people who are educators, who are excellent at developing new courseware and keeping themselves up to date,” she said.
“This is a bleeding-edge industry,” DeSimone said. “So they're constantly updating their skills, constantly updating their courses, and having to bring all the new things in.”
Online criminals, spying, industrial espionage and hacktivist groups are not going anywhere. Neither is cybersecurity. And they’re all growing industries in their own right.
Cyberattacks have also figured prominently in the Russian invasion of Ukraine, according to Google’s Threat Analysis Group.
“The Ukrainian government is under near-constant digital attack,” Google said in a February report. Russian-backed hackers have attacked the government and companies in Ukraine as the countries’ troops continue to fight with guns and bombs on the front lines. Google said cyberattacks against NATO countries are also up.
In the United States, hackers took down the Colonial Pipeline in 2020 in a ransomware attack, cutting off much of the gas supply to the East Coast. Several North Carolina counties have been knocked offline by similar attacks.
“Real lines got crossed when we started to see hospitals and schools and places that hadn't otherwise been touched by this sort of activity,” said Tripp, with Duke University’s IT security team.“Real lines got crossed when we started to see hospitals and schools and places that hadn't otherwise been touched by this sort of activity,” said Tripp, with Duke University’s IT security team.
Defenses against cyberattacks continue to evolve. But even at a top research university like Duke, the security experts can feel like they’re always one step behind the hackers.
Big networks are vulnerable because they serve lots of people. Each one of those people is a potential target that could help a hacker get into the system. Tripp said a big part of what they do is training their users, the students, staff and faculty that rely on Duke’s network every day.
To keep Duke’s network safe, Tripp said the future will be without passwords.
“One of the big things, when it comes to the phishing attacks, and the sort of thing we're dealing with in the future, is password authentication, getting rid of passwords, which is really a legacy technology at this point,” he said.
That future could mean using a personal cell phone with face recognition or a passcode to be able to login to a network or a laptop with a fingerprint reader. Taking static passwords out of the equation means there’s no password for hackers to steal.
But as cybersecurity experts have learned time and again, hackers will evolve along with the security measures. Cybercrime isn’t going anywhere.






